No products in the cart.
- Latest
- Trending
ADVERTISEMENT
Funds raised by ransomware attacks fell from $765.6 million in 2021 to $456.8 million in 2022, according to a new report from analytics firm Chainalysis.
Crypto-related ransomware attacks have seen a steep decline in success over the past 12 months.
The chart below shows the increase and decrease in funds obtained by ransomware attacks over the past six years. 2020 saw a dramatic increase as stolen funds reached $765 million, with a similar amount stolen by bad actors in 2021.
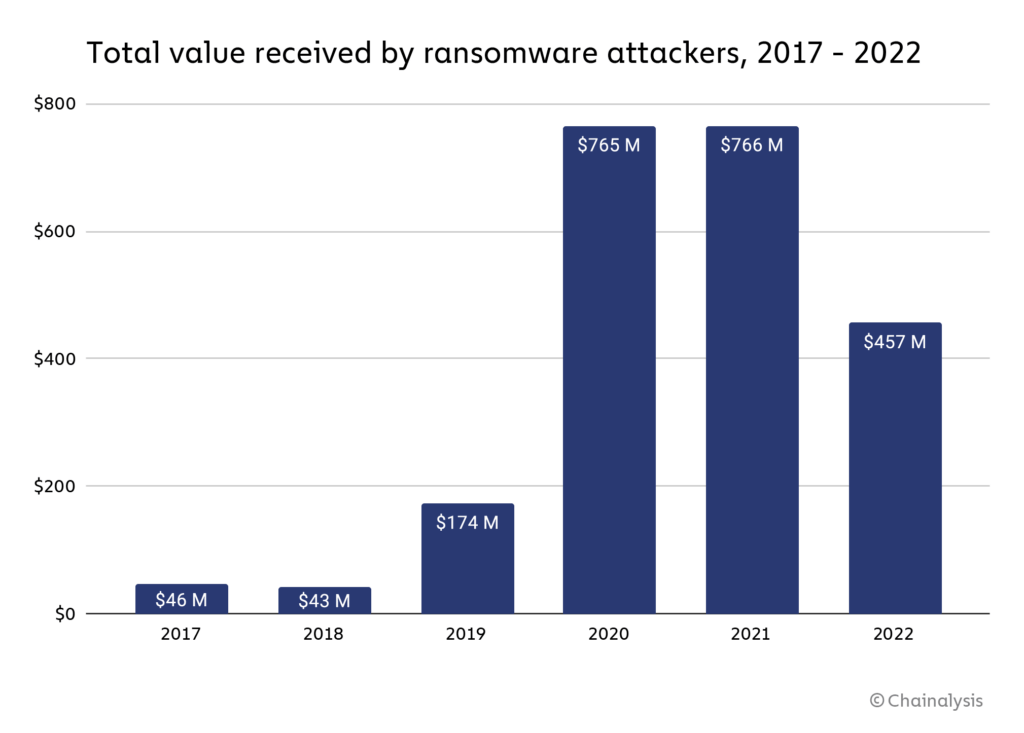
Chainalysis’s report acknowledges that the “actual total is much higher” because ransomware attackers likely own addresses that have not yet been identified, but this reduction is likely due to the damage. It shows that people are getting smarter against such attacks. As a result, Chainalysis released a statement supporting this opinion.
“[Ransomware payments falling] Attacks have not declinedwe believe much of the decline is due to victim organizations increasingly refusing to pay ransomware attackers. “
While payments to remove ransomware have dropped dramatically, the number of ransomware stocks has exploded in 2022.
Fortinet is a leading cybersecurity hardware and software company that report Over 10,000 unique strains active through 2022.
Strains have short lifespans as bad actors keep changing attack vectors to optimize the amount of stolen funds. For example, in 2012 the stock lasted his 3,907 days, but in 2022 the average length was just 70 days. As a result, cybersecurity solutions must respond to increased active tension in defense strategies.
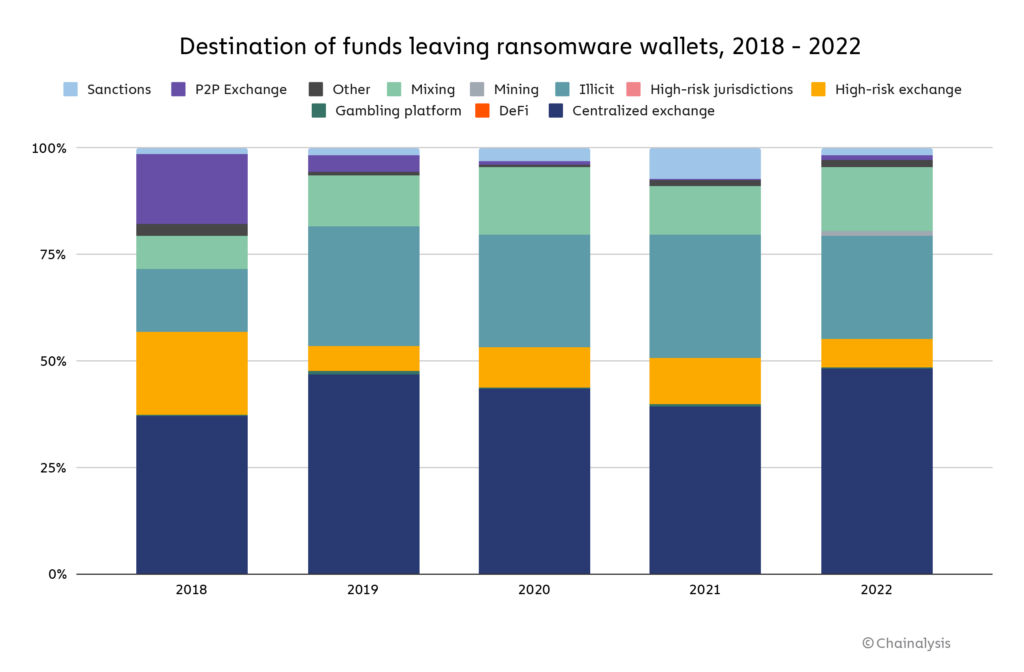
Funds obtained by ransomware attacks are laundered in several ways. Most of the funds are still going to popular centralized exchanges. However, his P2P exchanges, which were a popular solution for ransomware attackers in 2018, now make up a tiny fraction of the total number.
After centralized exchanges, the lasting method of money laundering is to use darknet markets designated as illegal in the Chainalysis chart below. Finally, mixing services are the next big thing, allowing attackers to wash out crypto with little recourse from global authorities.
Chainalysis used on-chain data to identify an affiliate market for ransomware software. This allows third parties to receive a small fixed income in the model of delivering ransomware as a service.
You can think of this as the gig economy, but its for ransomware. It might be an illusion, but in reality they are all the same car.”
On-chain data could allow companies like Chainalysis to track bad actors across the blockchain and identify their next attack vector. For example, the ransomware epidemic Conti was discontinued in May 2022.
Ransomware attackers reused wallets for multiple attacks, nominally launched in different attacks, making their tracking efforts relatively basic.
A better understanding of the landscape, improved security measures, and better on-chain forensics capabilities have reduced the number of successful ransomware attacks. As a result, victims have refused to pay the attackers, many of whom are associated with OFAC-sanctioned parties.
In 2019, only 24% of victims refused to pay, but by 2022 that percentage has increased to 59%. Paying ransomware bounties to parties on OFAC’s sanctions list can be “legally riskier.” Allan Lisk, Intelligence Analyst at Recorded Future, told Chainalysis:
With the looming threat of sanctions, there is the additional threat of legal consequences for payments. [ransomware attackers.]”
The consequences of not paying ransomware demands can often be devastating to victims who lose access to critical data. It is expected that the number of victims will decrease as well.
Regardless, the role of cryptocurrencies in ransomware attacks is clear. This is how hundreds of millions of dollars worth of cryptocurrencies are stolen every year. However, it is not without loss of traditional financial assets, many of which cannot be traced through blockchain.
Copyright © Pbird Media | Copyright © All rights reserved 2024

Copyright © Pbird Media | Copyright © All rights reserved 2024