No products in the cart.
On-chain analysis It shows that the North Korean hackers involved in hacking Harmony’s Horizon Bridge spent the weekend trying to move some of the illicit funds.
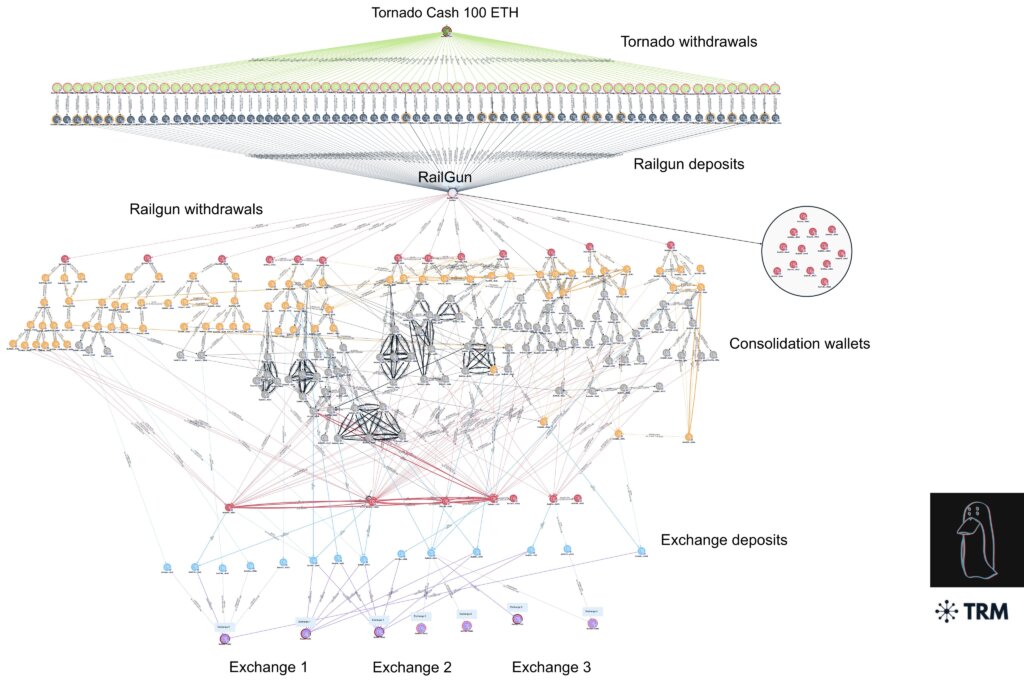
use railgunin a smart contract system that kicks off what’s known as “zero-knowledge proofs,” hackers attempted to move illicit funds through six different exchanges, some of which were reported over the weekend.
At least two exchanges, Binance and Huobi, were able to move quickly and freeze at least some of the laundered funds.
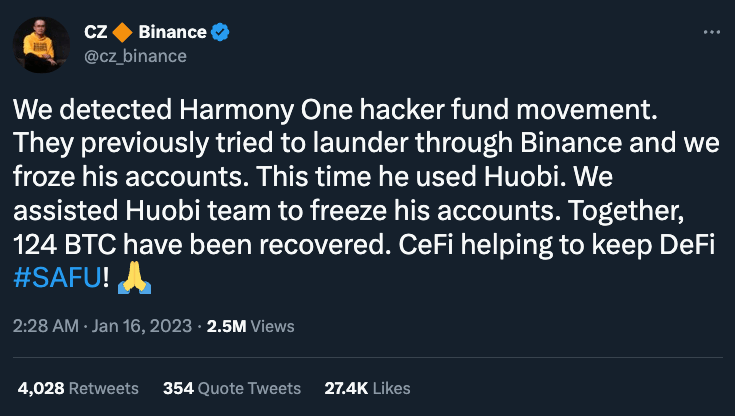
The move comes more than a week after the FBI. Declared The Lazarus group, which has ties to the Democratic People’s Republic of North Korea (DPRK), was responsible for exploiting Harmony’s Horizon Protocol, which lost more than $100 million in total cryptocurrency in June 2022 attacks.
That and similar attacks have fueled North Korea using illegal activities, including cybercrime and cryptocurrency theft, to generate income for the regime, the FBI claims.
Since 2017, $1.2 billion worth of cryptocurrency has been stolen by the group. Associated Press report.
The largest was a $624 million hack last April.
Bridge attacks have become increasingly common since decentralized finance (DeFi) became popular.
What are the common types of bridge exploits?
Bridge exploitation in the blockchain world is highly predictable, often due to code bugs or compromised cryptographic keys. Some of the most common bridging exploits include:
- fake deposit: In this scenario, malicious actors create fake deposit events without actually depositing funds, or use worthless tokens to infiltrate the network. hack January of last year.
- Validator flaw: The bridge validates the deposit before allowing the transfer.Hackers can exploit flaws in the verification process by creating fake deposits that occur during wormholes hack A digital signature verification flaw was exploited.
- validator takeover: Here the attacker looks for vulnerabilities by trying to control the majority validators by taking over a certain number of votes to approve new transfers. The Ronin Network hack is an example where 5 out of 9 validators were compromised.
However, it’s important to note that the most common factor across exploits is human error. Post-hack investigations don’t focus solely on bridge shortcomings, and security fixes can usually be patched, but only after the damage has already been done.
The scale of these exploits is a concern for blockchain developers. Other notable bridge exploits for 2022 and beyond include:
- February: Wormhole $375 million
- March: Ronin Bridge $624 million
- August: Nomad Bridge $190 million
- September: Wintermute $160 million